Challenge
In an era where cyber threats are continually evolving and becoming more sophisticated, utility companies face the daunting task of advancing their cybersecurity measures to protect the integral operations of the electric grid. Keeping pace requires not only ongoing investments in cybersecurity but also an assurance that these investments are both impactful and cost-effective. Historically, the utility sector has struggled with quantifying the effectiveness of cybersecurity investments—a challenge compounded by the dynamic nature of the threat landscape and the critical nature of the infrastructure involved.
Our client initiated a research project in 2015 aimed at developing a robust cybersecurity metrics framework. Their journey, extending into the development of version two by 2018, was marked by a commitment to creating objective and consistent metrics that comprehensively address protection, detection, and response domains. Figure (1) complexity and the promise they hold for a secure grid, the client confronted significant hurdles. Extensive pilot testing and a detailed usability survey revealed two core issues: the laborious process of data collection and the pressing need for an industry-wide standardization of metrics.
As the cybersecurity landscape becomes increasingly perilous and complex, the challenge now is not only to refine these metrics but to transition them from a procedural burden to an operational necessity. This case study explores the critical next steps in this pivotal project—streamlining processes, achieving alignment with industry benchmarks, and transforming cybersecurity metrics from a theoretical framework to a practical, actionable tool that can reinforce the security posture of utilities on a global scale.
Solution
EagleTC delivered software development expertise to the client, playing a crucial role in the rollout and standardization of cutting-edge security metrics through a carefully designed pilot project. This effort was directed at reinforcing the utility sector’s security framework by putting into practice and benchmarking state-of-the-art security metrics.
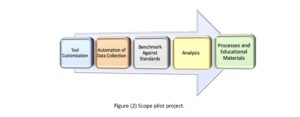
Spanning from 2019 to 2021, this pilot initiative aimed to systematically overhaul and enhance the cybersecurity protocols employed by utility companies. Figure (2) displays the scope of the pilot project.
The scope of the project encompasses several key development areas:
- Customizing the client’s metric calculation tool to align with the specific requirements of each utility company.
- Automating the data collection process to minimize manual efforts and enhance efficiency.
- Establishing benchmark procedures to enable a comparative analysis of security measures against industry standards.
- Leveraging advanced analytics to pinpoint and address opportunities to enhance security readiness.
- Developing detailed processes and educational materials to ensure the effective implementation of the tool and to foster widespread user acceptance.
Through EagleTC’s collaboration, the pilot project is not just operationalizing and benchmarking security metrics but also empowering utility companies to adopt a more proactive and informed approach to their cybersecurity strategies.
Results
The outcome of this venture emphasizes EagleTC’s competence to:
- Swiftly assemble and deploy a specialized team of experts, ensuring immediate engagement and start time of project.
- Rapidly deploy tailored tools and processes, accommodating immediate needs with minimal lead time.
- Provide the Utility company with a quantitative measure of the effectiveness of the security measure.
- Offer cost-effective, robust software development solutions that are aligned with the nuances of organizational and industry standards.
In essence, EagleTC exemplifies dedication to quality and adaptability, providing our clients with assurance that projects will progress seamlessly, upholding the highest standards of execution and punctuality.
